Leverage Cloud Solutions for Enhanced Information Safety And Security
In today's digital landscape, the ever-evolving nature of cyber threats requires a positive approach towards safeguarding delicate data. Leveraging cloud services provides an engaging option for organizations looking for to strengthen their information safety measures. By handing over trustworthy cloud provider with data administration, businesses can tap into a wealth of safety features and innovative modern technologies that bolster their defenses against destructive stars. The question occurs: just how can the usage of cloud solutions revolutionize information security methods and offer a robust guard against prospective vulnerabilities?
Significance of Cloud Safety And Security
Making certain robust cloud security actions is vital in securing sensitive information in today's digital landscape. As companies progressively count on cloud solutions to store and refine their information, the need for solid safety protocols can not be overstated. A breach in cloud protection can have serious consequences, varying from monetary losses to reputational damage.
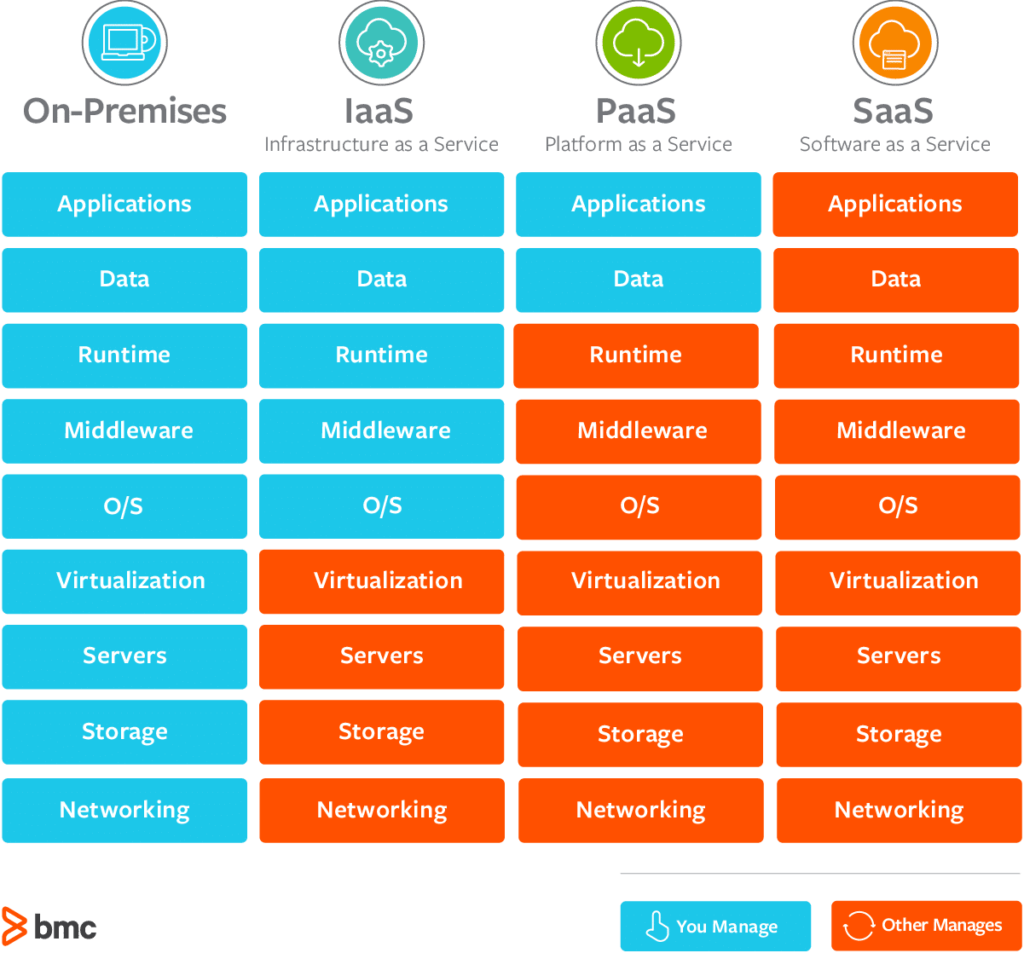
Among the primary reasons why cloud safety is vital is the common duty version employed by many cloud company. While the supplier is in charge of safeguarding the framework, customers are in charge of securing their information within the cloud. This division of duties underscores the significance of applying robust safety and security procedures at the customer degree.
Furthermore, with the expansion of cyber hazards targeting cloud atmospheres, such as ransomware and information breaches, organizations should stay alert and aggressive in mitigating dangers. This entails on a regular basis updating security methods, checking for questionable activities, and educating employees on ideal techniques for cloud safety and security. By prioritizing cloud security, companies can much better safeguard their sensitive data and promote the depend on of their customers and stakeholders.
Data File Encryption in the Cloud

File encryption in the cloud generally includes using cryptographic formulas to clamber information right into unreadable formats. This encrypted information can only be deciphered with the matching decryption trick, which adds an additional layer of security. In addition, lots of cloud service companies supply file encryption devices to protect data at remainder and in transit, boosting general information security. Executing robust file encryption practices together with other safety and security procedures can significantly bolster a company's defense versus cyber hazards and safeguard valuable details saved in the cloud.
Secure Data Back-up Solutions
Information back-up solutions play an essential duty in making certain the strength and security of information in case of unforeseen events or data loss. Secure data backup solutions are necessary components of a durable information safety technique. By consistently supporting information to safeguard cloud servers, organizations can reduce the dangers related to information loss due to cyber-attacks, hardware failings, or human mistake.
Applying safe and secure information backup services includes selecting reliable cloud service carriers that use security, redundancy, and information integrity steps. In addition, data stability checks guarantee that the backed-up information remains tamper-proof and unaltered.
Organizations ought to establish automatic backup routines to guarantee that data is consistently and effectively backed up without hand-operated treatment. When required, regular testing of data repair processes is additionally vital to guarantee the performance of the back-up solutions in recuperating data. By buying protected data backup services, companies can enhance their data safety position and decrease the influence of possible data breaches or disruptions.
Role of Accessibility Controls
Applying rigorous accessibility controls is important for maintaining the security and honesty of delicate details within business systems. Gain access to controls act as a crucial layer of protection versus unapproved access, guaranteeing that only licensed people can watch or adjust sensitive information. By defining who can gain access to details resources, companies can restrict the risk of information breaches and unauthorized disclosures.
Frequently assessing and upgrading accessibility controls is necessary to adjust to business changes and advancing protection risks. Constant monitoring and auditing of gain access to logs can help detect any type of suspicious tasks and unauthorized access efforts quickly. On the whole, robust gain access to controls are basic in protecting sensitive info and mitigating safety dangers within organizational systems.
Compliance and Regulations
On a regular basis ensuring compliance with relevant policies and criteria is important for companies to promote information safety and security and personal privacy procedures. In the realm of cloud services, where data is usually kept and refined on the surface, adherence to industry-specific regulations such as GDPR, HIPAA, or PCI DSS is important. linkdaddy cloud services.
Cloud company play a crucial duty in aiding organizations with compliance initiatives by offering services and attributes that line up with various regulative demands. As an example, lots of carriers offer security capacities, gain access to controls, and audit tracks to assist companies satisfy information safety criteria. Furthermore, some cloud solutions undergo routine third-party audits and accreditations to show their adherence to sector guidelines, offering added guarantee to companies seeking compliant solutions. By leveraging certified cloud solutions, organizations can improve their information security pose while satisfying governing commitments.
Conclusion
In final thought, leveraging cloud solutions for boosted information protection is essential for companies to protect sensitive information from unauthorized accessibility and potential violations. By implementing robust cloud protection protocols, consisting of information security, safe backup solutions, accessibility controls, and compliance with guidelines, businesses can benefit from innovative security actions and expertise supplied by cloud provider. This helps mitigate threats properly and guarantees the confidentiality, integrity, and availability of data.
Data backup solutions play an important duty in guaranteeing have a peek here the strength and safety and security of data in the event of unforeseen occurrences or information loss. By consistently backing up information to safeguard cloud servers, organizations weblink can alleviate the threats linked with information loss due to cyber-attacks, equipment failures, or human mistake.
Executing safe data backup remedies involves choosing trusted cloud service carriers that offer file encryption, redundancy, and information stability steps. By spending in safe information backup options, services can improve their information safety posture and lessen the impact of potential information violations or disruptions.